Zero Trust Network Access
View solutionZTNA taken a step further: ZTRA - Zero Trust Remote Access
Leave the data where it can be better "guarded" - in the company or in a cloud environment that can be controlled by the company. This also makes it easier to comply with the GDPR.
Then use SparkView in the company to access the applications and data, because SparkView works in principle like a terminal in the browser, i.e. the application to be operated is on the target system and the data also remains there. No additional software needs to be installed on the user's terminal, and none on the target systems.

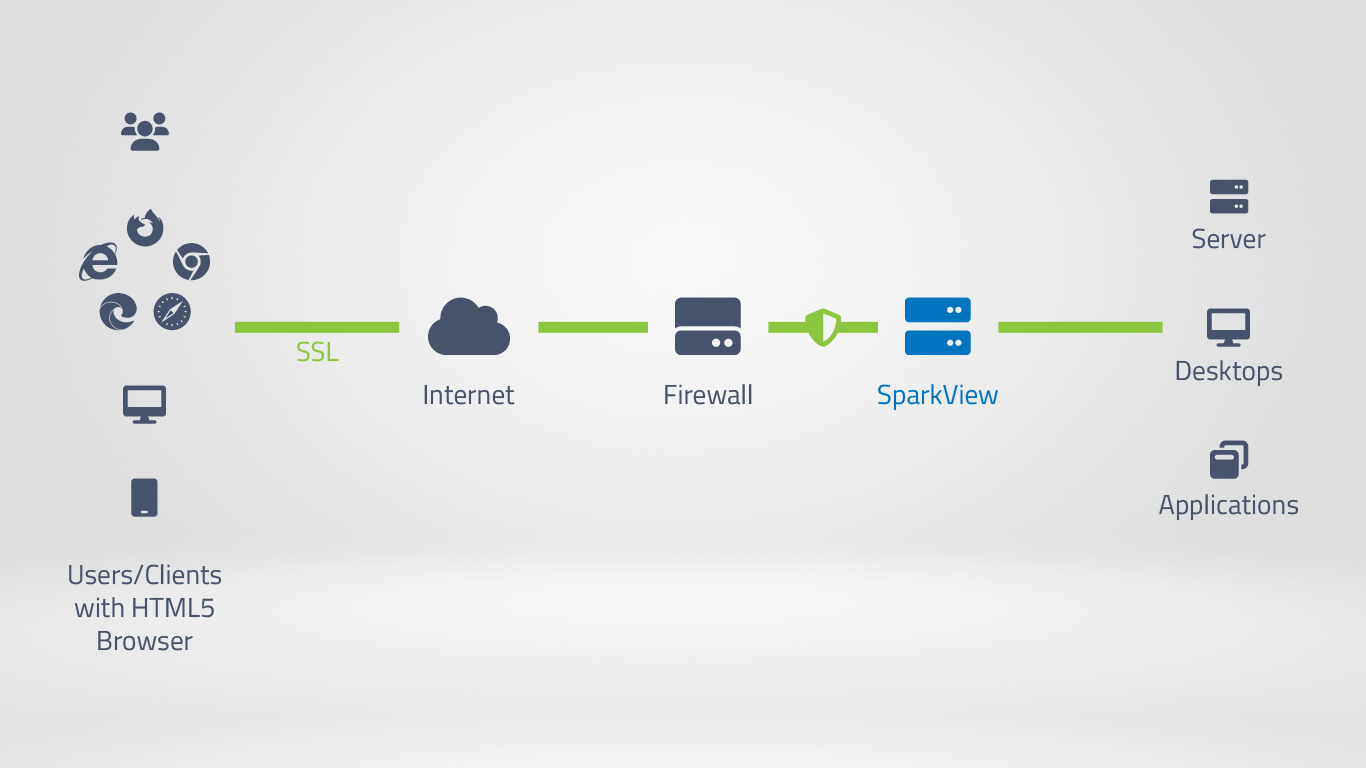
How does ZTRA work with SparkView?
Only keyboard and mouse inputs are sent from the client, and the screen contents are then transmitted to the user's browser. The target system, e.g. a Windows desktop or server, does the computing. The data remains on the server in the company.
In addition to significantly lower bandwidth requirements, this also means that much less expensive end devices can be used, e.g. Chromebooks or tablets.
Additional security through two-factor authentication
Hacker attacks are becoming more and more commonplace and also more intelligent, not only large companies are attacked on a daily basis. User names and passwords alone are no longer enough to effectively protect your company from such attacks.
Two-factor authentication significantly improves security against attacks, because in addition to what you know (username, password) you need another component (e.g. a smartphone) to gain access to your company resources.
In principle, it works like credit card payments. You can only take the "goods" if you have a card and know the PIN. Therefore, be sure to add two-factor authentication to the login process for security.
With ConeXa, we offer a solution that is installed and managed on-site, ensuring full enterprise control of all key components for secure remote access. Of course, ConeXa works harmoniously with SparkView.
Together, the two solutions form the core of our Zero Trust Remote Access offering.
If you are already using or wish to use another 2FA solution, SparkView can be integrated there as well.
Contact us
If you have a question, want to request a free demo or have other inquiries, feel free to contact us!

